In today’s digital world, protecting your online privacy is more important than ever. Creating anonymous accounts with encrypted email helps safeguard your personal information and prevent tracking. Here’s how to get started:
Key Steps to Stay Anonymous Online:
- Use Encrypted Email Providers: Choose services like ProtonMail or Tutanota for secure, private communication.
- Pick a Random Email Address: Avoid using personal details like your name or birthday.
- Set Up Securely: Use tools like Tor Browser or a VPN to hide your IP address during registration.
- Skip Recovery Options: Don’t link your account to a phone number or recovery email.
- Use Disposable Phone Numbers: Services like MobileSMS.io provide temporary numbers for SMS verification without exposing your real contact info.
Why It Matters:
- Regular email providers often scan your inbox for data and may cooperate with government requests.
- Encrypted email ensures your messages and metadata remain private.
- Disposable phone numbers prevent linking your accounts to your real identity.
Why Use Encrypted Email for Anonymous Accounts?
When setting up anonymous accounts, the email provider you choose can make or break your privacy efforts. Encrypted email services take a completely different approach to protecting your identity compared to traditional providers. Let’s break down the key advantages of encrypted email and the risks of sticking with regular services.
Benefits of Encrypted Email
Encrypted email services provide end-to-end encryption, which ensures that only you and your intended recipient can access the content of your messages. Unlike standard email providers, these services transform your messages into a coded format that’s unreadable to anyone else. As cybersecurity experts at Darktrace explain:
"Email encryption is a critical component of modern cybersecurity, protecting sensitive information exchanged through email communications."
This protection doesn’t stop at the content of your emails. Encrypted services also obscure metadata – like when and where emails are sent – offering an additional layer of privacy.
Another major benefit is the ability to sign up anonymously. Many encrypted email providers don’t require personal details, phone numbers, or recovery emails during registration. This eliminates the digital footprint that traditional email services typically create.
Lastly, jurisdiction matters. Many encrypted email providers are based in countries with strong privacy laws, offering further protection against government surveillance and unauthorized data requests.
Risks of Regular Email Providers
On the flip side, using traditional email services comes with significant privacy risks. Providers like Google handle over 100 billion emails daily, relying on data-heavy business models that clash with the goals of anonymity.
Data monetization is a key concern. Regular email providers scan your inbox for keywords to serve targeted ads and build detailed user profiles. This practice creates a permanent record of your communications, closely tied to your identity. Additionally, these services often require personal details – like phone numbers – during signup, further compromising anonymity.
Another issue is weak encryption. While many traditional providers use SSL/TLS to protect server connections, they often store your emails in plaintext on their servers. This leaves your messages vulnerable to unauthorized access.
Finally, regular email providers are more likely to cooperate with government data requests. This makes them a poor choice for anyone prioritizing privacy and anonymity.
The stark differences in how encrypted and traditional services handle security and privacy highlight why encrypted email is the better option for maintaining anonymity online.
How to Set Up an Encrypted Email Account
Encrypted email is a powerful tool for maintaining privacy online. If you’re looking to set up a secure and anonymous account, you’ll need to pick the right provider, register carefully, and follow some essential privacy practices.
Picking a Privacy-Focused Email Provider
The first step is choosing an email provider that prioritizes privacy. Two popular options are ProtonMail and Tutanota, both known for their strong encryption and privacy features.
- ProtonMail (based in Switzerland): Offers zero-access encryption, meaning even the provider can’t read your messages. It includes a free plan and affordable upgrades.
- Tutanota (based in Germany): Goes a step further by encrypting not only the email content but also subject lines. However, it doesn’t support the standard IMAP protocol, which may limit compatibility with certain email clients.
When selecting a provider, look for features like two-factor authentication, metadata removal, and anonymous payment options. Also, consider the provider’s server location – countries like Switzerland, Germany, and Norway have strong privacy laws that can enhance your security.
Step-by-Step Sign-Up Process
To create your encrypted email account while staying anonymous, follow these steps:
- Use Privacy Tools: Start by accessing the internet through the Tor Browser and a VPN. Clear your browser data before proceeding to remove any traces of your activity.
- Choose an Anonymous Email Address: Avoid using identifiable patterns like your name or birth year. Instead, go for a random combination of letters and numbers.
- Create a Strong Password: Use at least 12 characters, mixing letters, numbers, and symbols. Avoid dictionary words or anything tied to your personal life. Store your recovery codes securely, but not on your computer.
- Disable Non-Essential Features: During registration, skip options like contact syncing or calendar integration, as these can compromise your anonymity.
Once your account is set up, you’re ready to use it while maintaining privacy.
Tips for Staying Anonymous
After registration, it’s important to follow best practices to protect your identity:
- Access Securely: Always log in through Tor or a VPN. Change your VPN server or Tor circuit frequently to avoid leaving a digital trail.
- Keep It Separate: Don’t link your encrypted email to personal devices, accounts, or services. Avoid using it for platforms that require real-world verification or are tied to your regular email.
- Skip Recovery Options: Avoid adding recovery emails or phone numbers to prevent connecting your anonymous account to your real identity.
- Scrub Attachments: Before sending files, remove metadata, which can reveal details like your location or device.
- Pay Anonymously: If you upgrade to premium features, use anonymous payment methods such as cryptocurrency or prepaid gift cards bought with cash. Avoid credit cards or other traceable payment options.
Lastly, stay vigilant. Regularly update your password, monitor for unusual activity, and keep an eye on any updates to your provider’s security policies. By following these steps and tips, you can enjoy the benefits of encrypted email while keeping your identity protected.
Using Disposable Phone Numbers for Verification
Once you’ve set up your encrypted email, many platforms will still require SMS verification. This step, while common, can jeopardize your anonymity unless you use a disposable phone number.
Why Disposable Numbers Are Important
Encrypted email keeps your communications private, and disposable phone numbers do the same for your verification process. These days, most online services ask for phone number verification to prevent fraud. While this helps them, using your personal number ties your identity to your anonymous accounts.
Disposable numbers act as a shield, keeping your personal contact information out of reach. They protect against spam calls and texts that often follow sign-ups and reduce the risk of your data being exposed. Once you’ve completed the verification, you can simply discard the number, cutting off any unwanted communication. This added layer of privacy makes it harder for cybercriminals to piece together your personal details, offering extra protection against identity theft.
"Using disposable phone numbers provides an essential layer of protection and peace of mind. These temporary numbers serve as a buffer between your real contact information and the online world, effectively shielding your personal details from potential misuse and enhancing both privacy and security when engaging with various online services." – Ronald Meyer
Think about the bigger picture: over 80% of security breaches are linked to weak, reused, or stolen passwords. Combine that with incidents like the massive July 2024 breach that exposed over 10 billion passwords, and it becomes clear how critical it is to protect every piece of personal information. Your phone number, often used for password resets and account recovery, is a prime target for attackers.
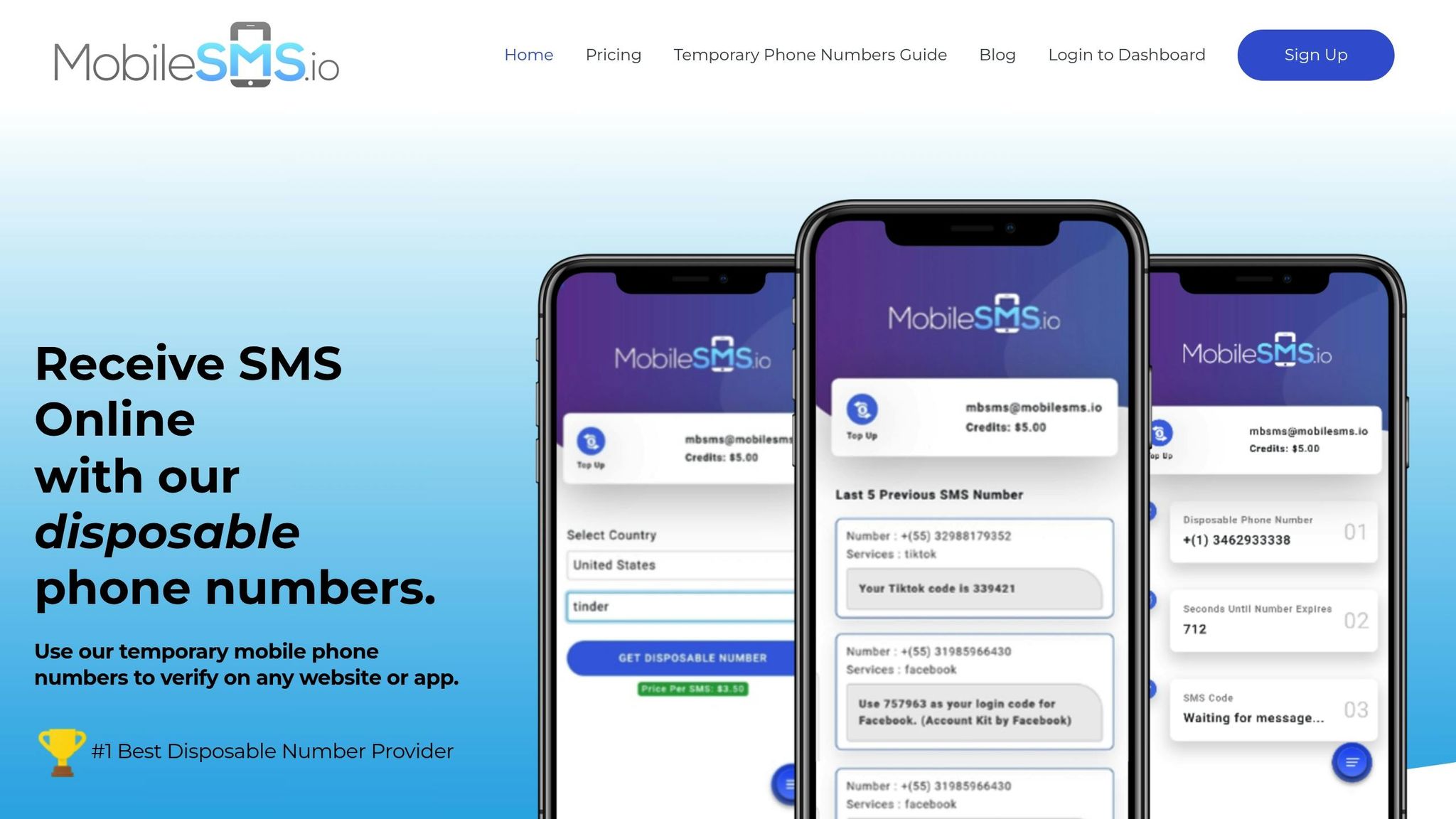
How MobileSMS.io Keeps Your Privacy Intact
Many platforms now block VoIP numbers to prevent fraud, which makes traditional internet-based phone services unreliable for verification. MobileSMS.io solves this problem by providing real SIM-card-based numbers that verification systems treat like regular phone numbers.
Since 2018, MobileSMS.io has earned the trust of thousands of users by offering dependable SMS verification numbers. These numbers work with over 1,200 platforms, including major services like Google, Telegram, WhatsApp, Facebook, and Instagram – all of which often reject VoIP numbers.
The service covers numbers from over 100 countries, with a focus on U.S.-based options while also offering international selections. Whether you need a one-time number or a long-term rental for ongoing use, MobileSMS.io caters to different privacy needs.
What stands out is their clear pricing model. You only pay when you successfully receive a verification code – no hidden fees. If a number doesn’t work for your chosen platform, you get a refund. This pay-as-you-go system ensures you’re never charged for failed attempts, making it both budget-friendly and reliable.
For those managing multiple accounts or working in teams, MobileSMS.io also supports Slack and Discord integration, letting you handle verification codes collaboratively while maintaining privacy.
Using MobileSMS.io for SMS Verification
MobileSMS.io offers a simple and efficient way to handle SMS verification securely. Here’s how to get started:
- Set up your account: Sign up for MobileSMS.io and add credits. The minimum deposit is $5.00, and charges only apply when SMS codes are successfully received. Costs vary by platform and country, with U.S.-based numbers typically priced between $4.00 and $5.50.
- Verify your account: Log into the MobileSMS.io dashboard, select your desired country and platform, and click "Get One-Time Use Number" to start a 10-minute timer. Use this number for verification, and once the SMS arrives, it will appear on your dashboard.
Some countries even allow you to receive a second SMS during the 10-minute window by clicking "Receive Another SMS" if needed. Once you’re done, the number is automatically discarded, ensuring no further communication can reach you.
For added privacy, use a VPN to match your IP address to the country of your chosen number. If you need repeated verifications from the same service, consider the long-term rental options MobileSMS.io offers.
Pro tip: After verifying your account, remove the phone number from the service settings and switch to a TOTP (Time-based One-Time Password) method for ongoing two-factor authentication. This disconnects your account from any phone number while keeping it secure.
MobileSMS.io also provides free options to test the service, including free numbers for the UK, two free U.S. numbers, and a free Germany number. This lets you try the platform before committing to paid options.
sbb-itb-5a89343
Best Practices for Staying Anonymous
Taking initial precautions like setting up encrypted email accounts and using disposable phone numbers is a good start, but maintaining anonymity is an ongoing effort. To truly minimize your digital footprint, you’ll need to adopt consistent habits and practices that go beyond the basics.
Using Secure Communication Methods
Protecting your IP address is essential. Tools like VPNs and the Tor browser can help. A VPN reroutes your internet traffic through secure servers in different locations, masking your actual IP address with the VPN server’s. Meanwhile, the Tor browser takes it a step further by encrypting your connection multiple times and routing it through a network of volunteer-operated servers. This makes it incredibly hard for anyone to track your online activity.
To further protect yourself, disable JavaScript in your browser when possible, as it can be exploited to reveal system details. Also, consider using separate browsers for different purposes – this helps compartmentalize your data and prevents overlap between your anonymous and personal activities.
Removing Metadata Traces
Every file you share – whether it’s an image or a document – can contain hidden metadata that reveals more than you’d like. This data might include GPS coordinates, device information, timestamps, or even the author’s name. Before sharing files, make sure to strip out this metadata.
For an extra layer of protection, encrypt your files before uploading them to cloud storage. This ensures that even if the files are compromised, the information remains unreadable. Be cautious when writing email subject lines or content, as including personal details could accidentally expose your identity.
Regular Privacy Maintenance
Maintaining anonymity isn’t a one-and-done effort – it requires regular upkeep. If you’re using public or shared devices, clear your browser data to prevent any link between your anonymous activities and your real identity. Use strong, unique passwords for each account, and manage them with an offline password manager. Disable third-party cookies and browser fingerprinting, and keep all your software – whether it’s your operating system, email client, or security tools – updated to patch vulnerabilities.
It’s also important to monitor your anonymous accounts for any unusual activity. Check login logs and account settings regularly. If something seems off, change your passwords immediately or consider setting up new anonymous accounts. Avoid linking these accounts to any social media profiles, as doing so could inadvertently reveal personal details.
For the best results, limit how long your anonymous accounts remain active. The longer an account exists, the more data it accumulates, increasing the risk of exposure. Periodically create new accounts and securely delete old ones to maintain your privacy.
Conclusion
Using anonymous accounts with encrypted email is a smart way to strengthen your online privacy. Pairing encrypted email providers with disposable phone numbers, like those from MobileSMS.io, creates a strong shield against potential cyber threats.
Here’s a sobering fact: 94% of organizations reported phishing attacks in the past year. Relying on regular email services for account creation can leave your personal details vulnerable to cyberattacks and data breaches, putting your identity at risk for years.
By combining encrypted email with disposable numbers, you’re adding important layers to your privacy strategy. Encryption ensures your communications remain secure, while disposable numbers keep your verification process private. This approach helps you avoid spam, protect your identity, and manage multiple accounts without exposing your real contact information.
"An anonymous email address must not be linked to a name or an IP address. When creating an anonymous email address one must not use personally identifiable information upon registration. The email provider must not log IP addresses and strip IP addresses from emails sent to qualify as anonymous." – Tuta
The steps shared in this guide are designed to work together, creating multiple layers of protection. Each layer makes it harder for anyone to connect your online activities to your real identity.
Staying anonymous online requires more than just tools – it demands strong passwords, careful habits, and ongoing vigilance. As the digital world continues to change, so do the threats. Keeping your privacy practices up-to-date is essential to maintaining your anonymity in an ever-evolving online environment.
FAQs
How do encrypted email services keep my information private compared to regular email providers?
Encrypted email services protect your privacy by using encryption to turn your messages into unreadable code. This ensures that only the person you’re sending the email to can decode and read it. This method, known as end-to-end encryption, keeps your information secure, even if someone intercepts the message while it’s being sent.
On the other hand, many traditional email providers send messages as plaintext, which makes them easier to intercept and access without permission. By switching to encrypted email services, you can keep sensitive information out of the hands of third parties and take better control of your privacy and security.
What steps can I take to stay anonymous after setting up an encrypted email account?
To keep your identity private after setting up an encrypted email account, make sure to use a VPN or Tor to hide your IP address. Also, avoid using any personal information when creating your email address. It’s important not to connect your encrypted email to accounts that could reveal who you are or to share sensitive details unless absolutely necessary.
For extra protection, turn on two-factor authentication using an authenticator app, update your passwords regularly, and think about using disposable email addresses for situations where you only need them temporarily. These steps can help shield your privacy and reduce the chances of breaches or tracking.
Why should I use disposable phone numbers for SMS verification, and how does MobileSMS.io protect my privacy?
Using disposable phone numbers for SMS verification is a smart way to protect your personal information. It keeps your real number hidden, lowering the chances of spam, phishing attacks, or data breaches. A temporary number acts as a shield, keeping your identity separate from the online services you use.
MobileSMS.io takes your privacy a step further by providing non-VoIP, SIM-based numbers that work seamlessly with major platforms. These numbers are meant for short-term use, helping you keep your personal details private and reducing the risk of prolonged data exposure. Whether you’re signing up for apps, websites, or other online services, MobileSMS.io ensures you stay secure and under the radar.