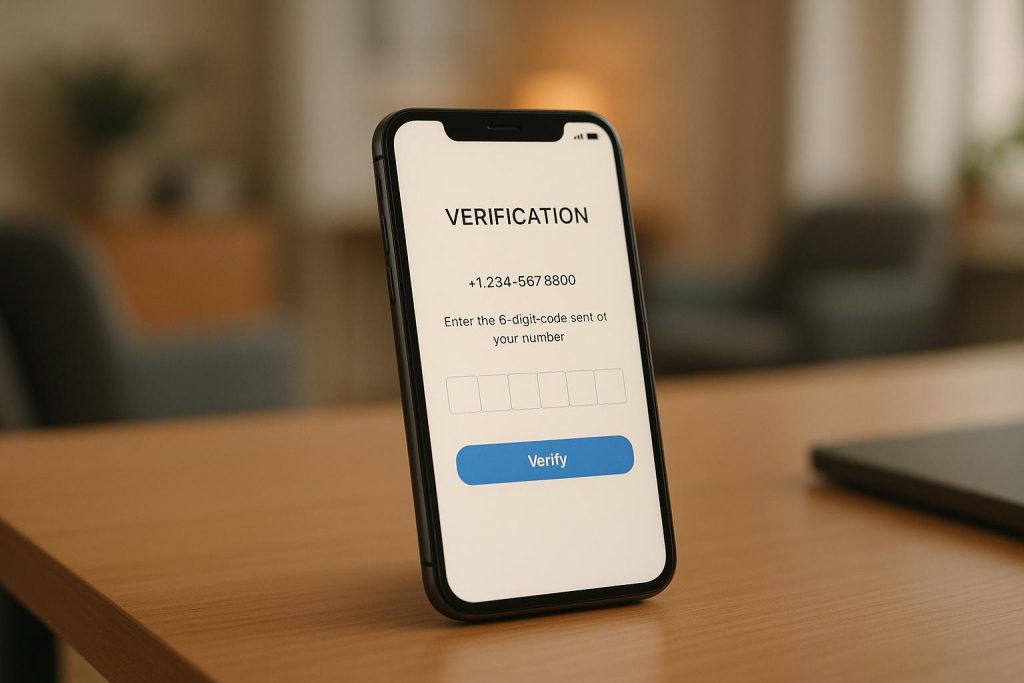
How Non-VoIP Numbers Work for Cross-Platform Verification
Explore the advantages of using non-VoIP numbers for secure cross-platform verification, ensuring safety and privacy in the digital age.
How Non-VoIP Numbers Work for Cross-Platform Verification Read More »